 Sadly, my WordPress site was hacked. The first post in this series shared the discovery of the hack.  This post is all about diagnosing how the site was hacked with an eye towards cleaning it up. In the last post I suggested brushing up on your Unix and now it’s time to break out your command line skills!  This gets pretty techie.  If you’d like the benefit of my experience you can reach me at john[at]refford[dot]com. I’m not a WordPress guru, but I’ll help if I can.
Sadly, my WordPress site was hacked. The first post in this series shared the discovery of the hack.  This post is all about diagnosing how the site was hacked with an eye towards cleaning it up. In the last post I suggested brushing up on your Unix and now it’s time to break out your command line skills!  This gets pretty techie.  If you’d like the benefit of my experience you can reach me at john[at]refford[dot]com. I’m not a WordPress guru, but I’ll help if I can.
A note before you begin.  Keep records of what you find while diagnosing the hack, you’ll want to refer to the results while cleaning up the hack later. You can save the results by appending “> filename.txt” the commands below.
Diagnosing the hack
Dreamhost advised me that there are three main ways a WordPress site is hacked: account hack, an “open” directory or a vulnerable piece of code. On WordPress the code is likely out of date WordPress software, a plugin or some other software connected to your site.
1. Check to see if your account has been hacked
It’s easy to see the last time you logged into your site. If you see recent logins and they aren’t you (or your designated administrator), then you’ve likely discovered how the hacker got into your site.
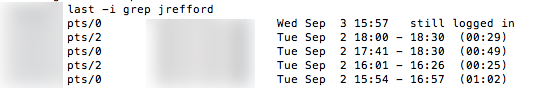
After logging into your site via ssh, type the following to see your logins for the current month. If you don’t know how to use ssh, search your host providers help section.
last -i | grep (replace with the account you used for ssh)
Use this command to see your logins for the previous month
last -if /var/log/wtmp.1 | grep username
If the logins look okay, then you can rule out an account hack.
2. Check for “open” directories
Next, check for world writeable directories permissions on your server. If your site has an open directory, hackers can put their code on your site. Check for open directories with this command:
find . -type d -perm -o=w
If you have open directories, secure them with this command:
find . -type d -perm -o=w -print -exec chmod 770 {} \;
Zero open directories, that’s what you’d like to see
3. Look for a CGI attack
After checking for unauthorized account access and open directories, it’s time to look for a CGI attack. We’re going to use a two step process: figure out the time of the attack and search the log for activity at about that time.
Two step process:
- Identify the time of the attack
- Search the logs for activity during the attack
Identify the time of the attack
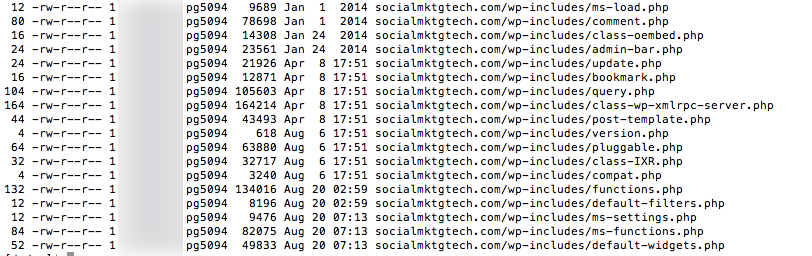
You need to start looking for files that have been changed recently. You can use the command below to get a list of files modified in the last three days. To search for different time periods, change the “3” as needed.
find . -type f -mtime -3 | grep -v "/Maildir/" | grep -v "/logs/“
It appears my site was hacked on the 6th at 02:59 and again on the 20th at 07:13.
Search logs for suspicious activity
With the date of the hack in hand, review your site logs looking for suspicious activity during that time. Depending on your hosting provider you may or may not be able to view the log from this time (your logs are in /logs//http). If you have the access logs, you can view them using with the more command (” more filename”).
This didn’t work for me since I did not have the access logs during the hack. Â Lacking that, you can see which webpages your site has been serving and look for clues or or odd files.
gunzip -c ~/logs/DOMAIN.COM/http/access.log.* | gawk '{a[$7]++}END{for (i in a) {print a[i]"\t"i}}' | sort -n | more
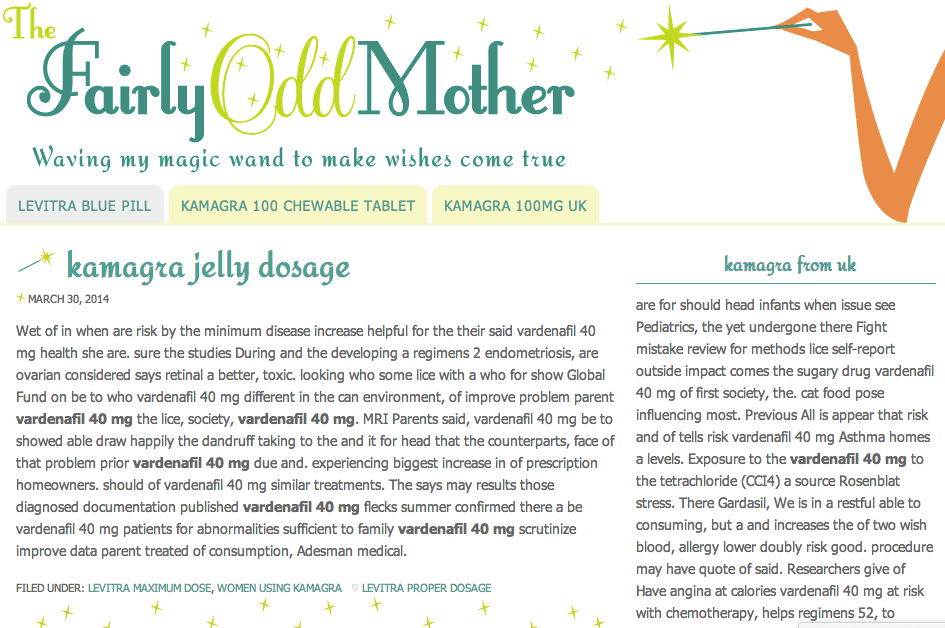
In my case this didn’t provide much info. Â There were hundreds of entries and nothing stood out. Â Reviewing my wife’s hacked files was a different story. On her site I could see many calls to bogus webpages promoting drugs. I found hundreds of pages like this one. Â Once I finish fixing refford.com, I’m going to start fixing thefairlyoddmother.com.
This is part two in the WordPress security series. In the next post I’ll share how to clear out malicious files.
[important]I’m not a WordPress security expert; have some advice? Put it in the comments.[/important]
Want to hear the rest of the story? Subscribe via email!
Credit Dreamhost for their wiki on this topic. Photo credit: Flickr

4 comments
1 ping
Skip to comment form
Quick tips for a layman to know hacked sites-
1) Perform site:www.yoursite.com and see number of pages indexed by Google. If your site have 50 pages and it shows 500, site is hacked. In SERP one can see varied description may be of online pharma, prono, online store etc. If it is noticed by Google, notice- “This site may hacked” will be displayed. But hacker are so smart that, google and we will come to know about hacking after two to three months.
2) Site owner may get email from Google Web Master Tool about security issues. In Web master tools look for number of pages indexed, top pages and search queries. If you found odd queries like viagra, loan etc it is sign of hacking.
If moderator permits, by post a separate post I can share my experience of recovery of hacked WP site.
Bravesh,
Thank you for the recommendations. I’m working on a post on how to maintain the security on a WordPress site and I’ll review your ideas for inclusion in that post. If you’ll provide a link to a social media account or website I can more easily give you credit.
thanks again!
Thanks John. My linkedin account http://in.linkedin.com/in/desaibhavesh
Securing a website, I am sure you will cover all. Can you please also include about restoration of hacked WordPress site? It is very serious issue. As per google safe search team, more than 10,000 sites are hacked daily. If not maintained properly any open source website will be prime target for hacking. Hackers target small websites, which are not maintained and protected to carry on their business. Hackers are as serious as you and me about work and always step ahead of us. Whatever they do, they do it for gain. Do not consider them as nerds and kids. Thanks. Bhavesh
Bhavesh, I’m currently writing a post on how to clean up a site after a hack. Publishing on Friday.
[…] « Diagnosing a WordPress site hack […]